2018 RCTF Write-Up
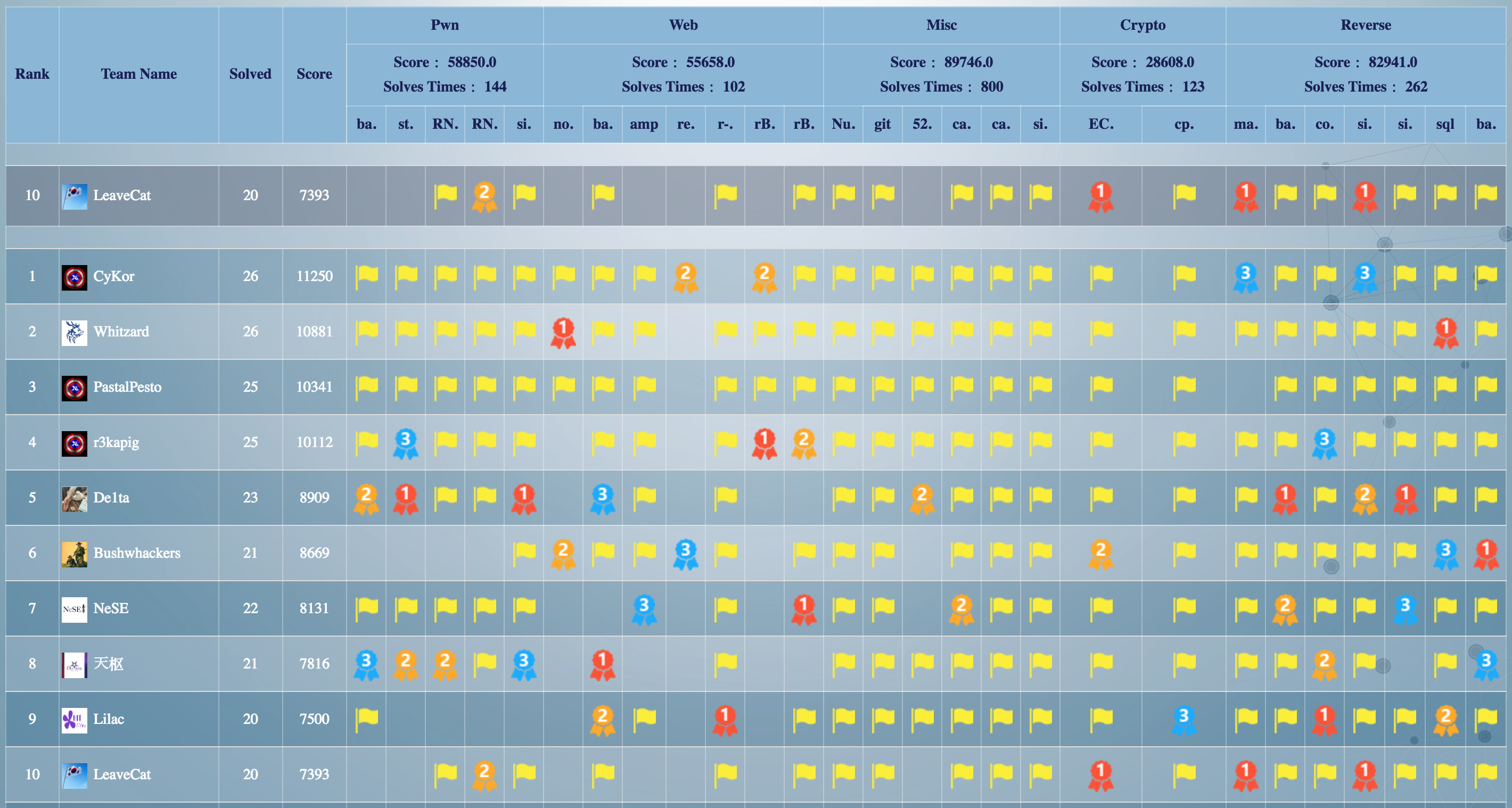
Participated as LeaveCat, Ranked 10th.
I solved 4 reverse challenge. (magic, simple-vm, simple-re, babyre2)
magic - 18 solved, 540 pt (first blood)
first stage : bruteforce to get correct timestamp. (analyzed sub_402357)
second stage : analyze vm and get flag. (analyzed sub_4023B1)
- stage1 bruteforce code
# run in windows os
import ctypes
dll = ctypes.CDLL("msvcrt.dll")
for time in range(0x5AFFE790, 0x5B028A90):
dll.srand(time)
table = [0x58, 0x71, 0x8F, 0x32, 0x05, 0x06, 0x51, 0xC7, 0xA7, 0xF8, 0x3A, 0xE1, 0x06, 0x48, 0x82, 0x09,
0xA1, 0x12, 0x9F, 0x7C, 0xB8, 0x2A, 0x6F, 0x95, 0xFD, 0xD0, 0x67, 0xC8, 0xE3, 0xCE, 0xAB, 0x12,
0x1F, 0x98, 0x6B, 0x14, 0xEA, 0x89, 0x90, 0x21, 0x2D, 0xFD, 0x9A, 0xBB, 0x47, 0xCC, 0xEA, 0x9C,
0xD7, 0x50, 0x27, 0xAF, 0xB9, 0x77, 0xDF, 0xC5, 0xE9, 0xE1, 0x50, 0xD3, 0x38, 0x89, 0xEF, 0x2D,
0x72, 0xC2, 0xDF, 0xF3, 0x7D, 0x7D, 0x65, 0x95, 0xED, 0x13, 0x00, 0x1C, 0xA3, 0x3C, 0xE3, 0x57,
0xE3, 0xF7, 0xF7, 0x2C, 0x73, 0x88, 0x34, 0xB1, 0x62, 0xD3, 0x37, 0x19, 0x26, 0xBE, 0xB2, 0x33,
0x20, 0x3F, 0x60, 0x39, 0x87, 0xA6, 0x65, 0xAD, 0x73, 0x1A, 0x6D, 0x49, 0x33, 0x49, 0xC0, 0x56,
0x00, 0xBE, 0x0A, 0xCF, 0x28, 0x7E, 0x8E, 0x69, 0x87, 0xE1, 0x05, 0x88, 0xDA, 0x54, 0x3E, 0x3C,
0x0E, 0xA9, 0xFA, 0xD7, 0x7F, 0x4E, 0x44, 0xC6, 0x9A, 0x0A, 0xD2, 0x98, 0x6A, 0xA4, 0x19, 0x6D,
0x8C, 0xE1, 0xF9, 0x30, 0xE5, 0xFF, 0x33, 0x4A, 0xA9, 0x52, 0x3A, 0x0D, 0x67, 0x20, 0x1D, 0xBF,
0x36, 0x3E, 0xE8, 0x56, 0xBF, 0x5A, 0x88, 0xA8, 0x69, 0xD6, 0xAB, 0x52, 0xF1, 0x14, 0xF2, 0xD7,
0xEF, 0x92, 0xF7, 0xA0, 0x70, 0xA1, 0xEF, 0xE3, 0x1F, 0x66, 0x2B, 0x97, 0xF6, 0x2B, 0x30, 0x0F,
0xB0, 0xB4, 0xC0, 0xFE, 0xA6, 0x62, 0xFD, 0xE6, 0x4C, 0x39, 0xCF, 0x20, 0xB3, 0x10, 0x60, 0x9F,
0x34, 0xBE, 0xB2, 0x1C, 0x3B, 0x6B, 0x1D, 0xDF, 0x53, 0x72, 0xF2, 0xFA, 0xB1, 0x51, 0x82, 0x04,
0x30, 0x56, 0x1F, 0x37, 0x72, 0x7A, 0x97, 0x50, 0x29, 0x86, 0x4A, 0x09, 0x3C, 0x59, 0xC4, 0x41,
0x71, 0xF8, 0x1A, 0xD2, 0x30, 0x88, 0x63, 0xFF, 0x85, 0xDE, 0x24, 0x8C, 0xC3, 0x37, 0x14, 0xC7]
for i in range(256):
table[i] ^= (dll.rand() & 0xff)
arr = []
for i in range(256):
arr.append([table[i], 0x7fffffff, 0])
cur_arr = arr[i]
if i & 0xf:
prev_arr = arr[i - 1]
else:
prev_arr = 0
if i >= 0x10:
prev16_arr = arr[i - 16]
else:
prev16_arr = 0
if prev_arr != 0 or prev16_arr != 0:
if prev_arr:
cur_arr[1] = (ctypes.c_int8(cur_arr[0]).value + prev_arr[1])
cur_arr[2] = prev_arr[2] * 2
if prev16_arr:
var = prev16_arr[1] + ctypes.c_int8(cur_arr[0]).value
if var < cur_arr[1]:
cur_arr[1] = var
cur_arr[2] = (prev16_arr[2] * 2) | 1
else:
cur_arr[1] = ctypes.c_int8(cur_arr[0]).value
if arr[-1][1] == 0x700:
print hex(time) # 0x5b00e398
correct timestamp is 0x5b00e398.
- stage2 reverse calculation code
enc = [137, 193, 236, 80, 151, 58, 87, 89, 228, 230, 228, 66, 203, 217, 8, 34, 174, 157, 124, 7, 128, 143, 27, 69, 4, 232]
table = [0x63, 0xef, 0xd5, 0xa2, 0x63, 0xb8, 0x17, 0xab, 0xd0, 0xc6, 0xd8, 0x50, 0xd1, 0x46, 0x97, 0xdf, 0xc4, 0x51, 0x1, 0xe0, 0x45, 0x78, 0xd8, 0x5f, 0xc4, 0xd8]
xor = 0x66
flag = ''
for i in range(len(enc)):
flag += chr((((enc[i] ^ xor) - 0xcc) ^ table[i]) & 0xff)
xor = ~xor & 0xff
print "rctf{h" + flag
vm is simply check our input.
when flag is correct, ascii art is printed that “rctf{h”.
flag : rctf{h@ck_For_fun_02508iO2_2iOR}
simple-vm - 44 solved, 317 pt (first blood)
simple vm, just analyzed.
- solve code
enc = [0x10, 0x18, 0x43, 0x14, 0x15, 0x47, 0x40, 0x17, 0x10, 0x1D, 0x4B, 0x12, 0x1F, 0x49, 0x48, 0x18, 0x53, 0x54, 0x01, 0x57, 0x51, 0x53, 0x05, 0x56, 0x5A, 0x08, 0x58, 0x5F, 0x0A, 0x0C, 0x58, 0x09]
table = bytearray("".join(chr(i) for i in range(32, 128)))
flag = ''
for i in range(len(enc)):
for j in range(len(table)):
a1 = ~((0x20 + i) & table[j])
a2 = ~(a1 & (0x20 + i))
a3 = ~(a1 & table[j])
a4 = ~(a3 & a2)
if a4 == enc[i]:
flag += chr(table[j])
print "RCTF{" + flag + "}"
flag : RCTF{09a71bf084a93df7ce3def3ab1bd61f6}
simple-re - 14 solved, 606 pt
it has a lot of anti debugging skill.
original code section was encrypted by xor and key is 0xcc.
it implement “SelfDebugging” anti reversing technique, so child process and parents process has debugger-debuggee relation.
sub_400B87 is just fake routine and real check routine is started at 0x400FDC.
and just analyze sub_401482, then we can get flag.
- solve code
def egcd(a, b):
if a == 0:
return (b, 0, 1)
else:
g, y, x = egcd(b % a, a)
return (g, x - (b // a) * y, y)
def modinv(a, m):
g, x, y = egcd(a, m)
if g != 1:
raise Exception('modular inverse does not exist')
else:
return x % m
mul_list = [0x556E4969, 0x2E775361, 0x893DAE7, 0x96990423, 0x6CF9D3E9, 0xA505531F]
res_list = [0x54A0B9BD, 0x4B818640, 0x8EB63387, 0xA9EABEFD, 0xB8CDF96B, 0x113C3052]
flag = ''
for i in range(len(mul_list)):
flag += hex(modinv(mul_list[i], 0x100000000) * res_list[i] & 0xffffffff)[2:].replace('L', '').decode('hex')[::-1]
print "RCTF{" + flag + "echn!qu3s}" # just guess... :p
last flag check function is too hard, so i guessed last flag block :p
flag : RCTF{5o_M@ny_an7i_Rev3rsing_Techn!qu3s}
babyre2 - 26 solved, 444 pt
it can solve using modular inverse.
- solve code
def egcd(a, b):
if a == 0:
return (b, 0, 1)
else:
g, y, x = egcd(b % a, a)
return (g, x - (b // a) * y, y)
def modinv(a, m):
g, x, y = egcd(a, m)
if g != 1:
raise Exception('modular inverse does not exist')
else:
return x % m
mul_list = [0x20656D6F636C6557, 0x2046544352206F74, 0x6548202138313032, 0x2061207369206572, 0x6320455279626142, 0x65676E656C6C6168, 0x756F7920726F6620]
res_list = [0x2B7192452905E8FB, 0x7BA58F82BD898035, 0xA3112746582E1434, 0x163F756FCC221AB0, 0xECC78E6FB9CBA1FE, 0xDCDD8B49EA5D7E14, 0xA2845FE0B3096F8E]
flag = ''
for i in range(len(mul_list)):
inv = modinv(mul_list[i], 0xFFFFFFFFFFFFFFC5)
flag += hex(res_list[i] * inv % 0xFFFFFFFFFFFFFFC5)[2:-1].decode('hex')[::-1]
print flag[:-3]
flag : flag{stay_prime_stay_invertible_away_from_bruteforce}
all source code uploaded in my github repository